Building your own Security Operations Center (SOC) is complex and expensive. With FusionOne’s SOC as a Service, you get the same capabilities – around the clock, run by Swiss security experts and seamlessly integrated into your existing Microsoft environment.
We continuously monitor your systems, detect threats in real time, respond immediately to incidents, and provide clear, easy-to-understand reports. This gives you enterprise-grade protection – without the effort and costs of running your own SOC.
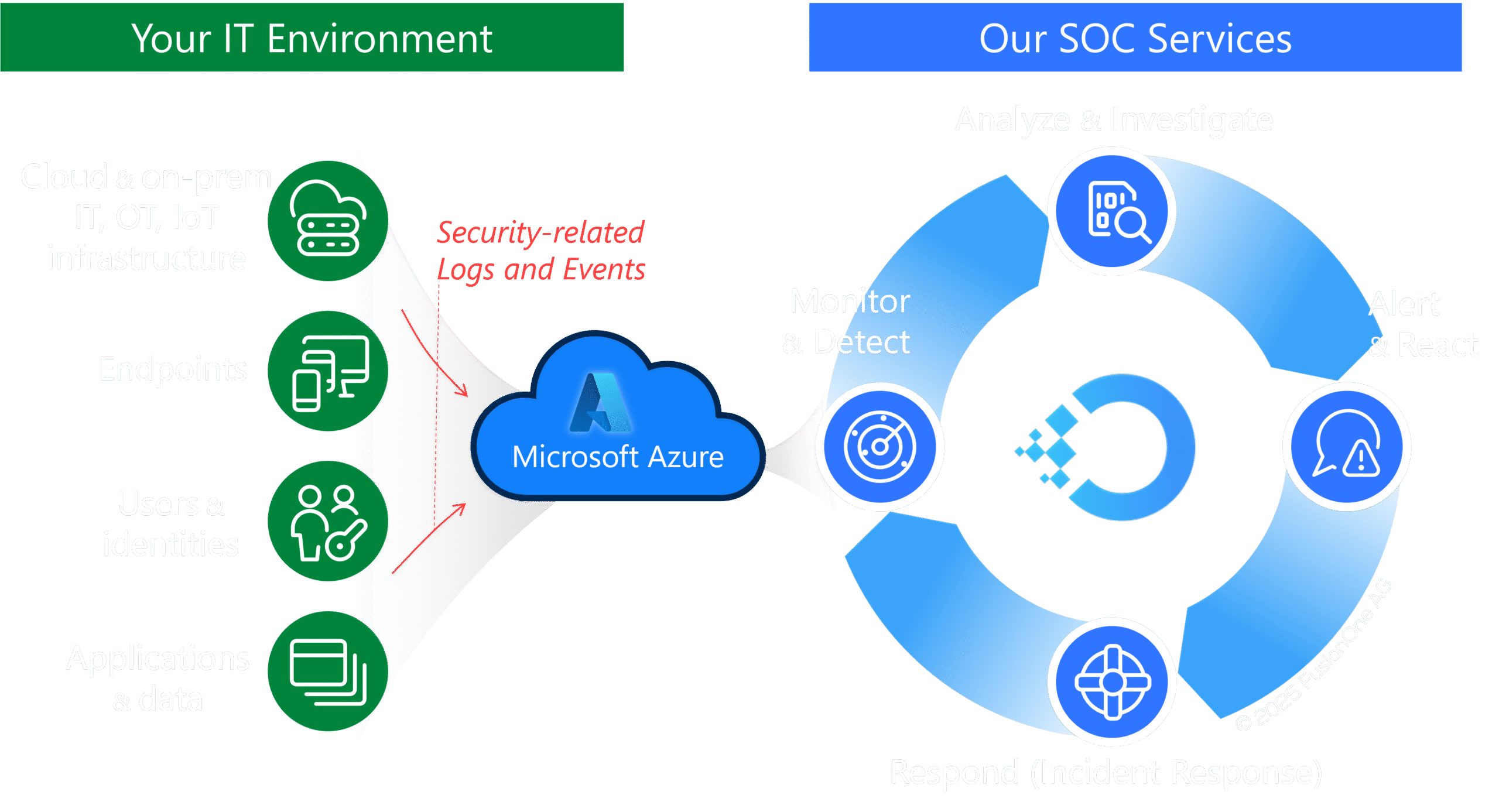
The customer environment is monitored and incidents are detected using leading tools and AI
Detected alerts and incidents are analyzed and investigated by experienced security analysts
If a true incident is detected, an alarm is raised and immediate measures are implemented (disrupt & contain)
In the event of critical incidents, the customer is well supported and - on demand - we directly call up the Cyber-Security Incident Response Team (see below)
At the heart of our SOCaaS offering is Microsoft Sentinel - our cloud-native SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation and Response) platform. Running directly in your Azure environment, Sentinel collects and analyzes security data from across your digital landscape. It delivers real-time threat detection, smart automation, and centralized visibility—allowing us to respond to threats quickly and efficiently, without the need for on-premises infrastructure.
Our SOCaaS integrates seamlessly with Microsoft Defender XDR and other endpoint protection platforms. When using Defender XDR, we benefit from a direct, bidirectional connection with Microsoft Sentinel—enabling real-time data sharing, automated response, and unified threat visibility across endpoints, identities, and cloud services. This tight integration ensures faster detection and more effective response to advanced threats.
Microsoft Sentinel uses AI to detect threats faster and smarter. Its AI analyzes behavior patterns, correlates attack stages, and supports custom machine learning models. With its new data lake, Sentinel enables scalable, cost-efficient security insights across platforms.
User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel uses machine learning to build behavior profiles for users, devices, and applications. It detects anomalies like unusual sign-ins or lateral movement, helping our SOC team quickly identify compromised assets and prioritize incident response.
Microsoft Sentinel integrates global and local Threat Intelligence (TI) to detect emerging threats early. Alongside Microsoft Defender Threat Intelligence, we use our own MISP-based TI platform to ingest Indicators of Compromise (IOCs) from over 70 feeds—including abuse.ch, AlienVault, and Emerging Threats. This dual-source setup ensures fast, AI-enhanced detection of new attack patterns across your environment.
Microsoft Sentinel enables us for proactive threat hunting through powerful search and analytics. Suspicious activity is identified using threat intelligence and MITRE ATT&CK correlations. Our SOC team conducts automated IOC-based scans and targeted investigations—supported by playbooks, livestreams, and bookmarks.
As part of our SOCaaS offering, we deliver monthly reports that provide clear insights into your security landscape. Each report includes incident statistics, severity breakdowns, and visual dashboards powered by Power BI. We summarize key findings, threat trends, and SOC activities in plain language - giving you a transparent view of what happened, what was investigated, and what actions were taken. This ensures you stay informed and in control without needing to dive into technical details.
Our Darknet Monitoring service - powered by Redguard - provides continuous surveillance of hidden forums, marketplaces, Telegram channels, and social media platforms. We actively search for data leaks and suspicious activity tied to your organization. Alerts are reviewed by our SOC and CSIRT team and reported promptly, helping you stay ahead of threats that surface beyond the visible web.
Our CSIRT - powered by Redguard - has all the expertise that is required in case of an incident (technology, regulatory provisions, etc.) and is constantly in contact with the authorities and other IR teams. Our specialists for Digital Forensics and Incident Response (DFIR) support you around the clock in containing and analyzing cyber incidents, especially in the event of a ransomware attack, and in restoring your business operations.
We use cookies to enhance your browsing experience, serve personalized ads or content, and analyze our traffic. By clicking 'Accept All', you consent to our use of cookies.

We will contact you as soon as possible

We will contact you as soon as possible with your tailor-made SOCaaS proposal
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.